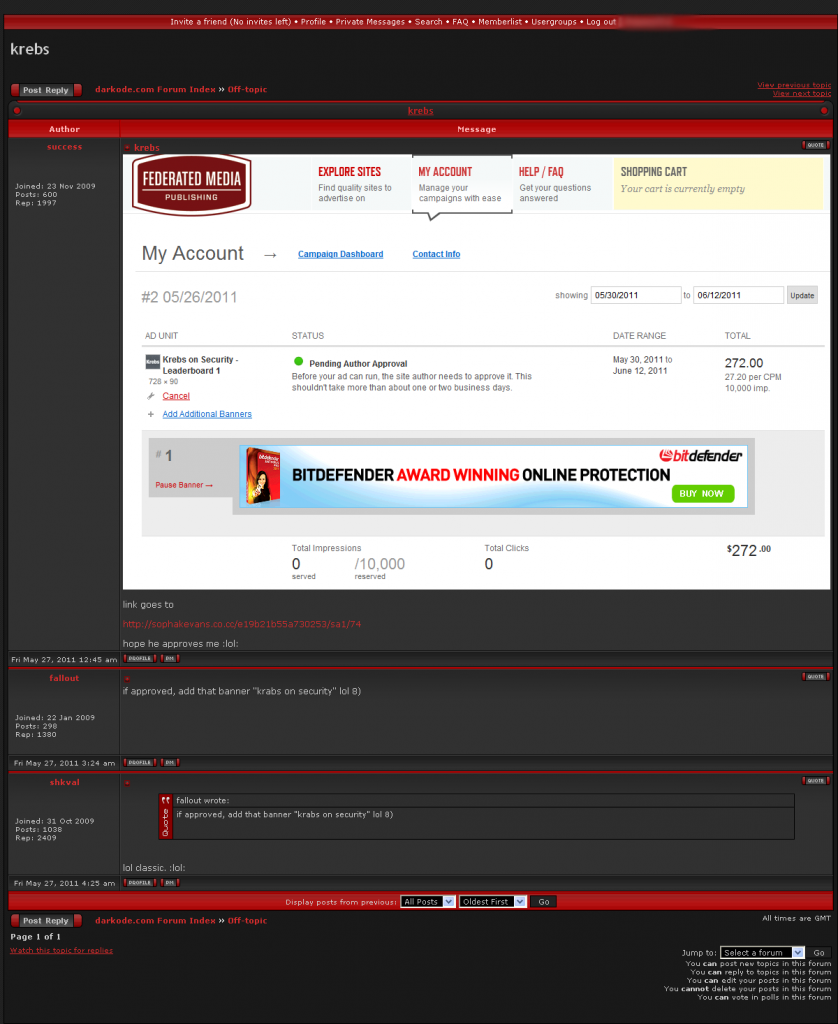
Members of an exclusive underground hacker forum recently sought to plant malware on KrebsOnSecurity.com, by paying to run tainted advertisements through the site’s advertising network — Federated Media. The attack was unsuccessful thanks to a variety of safeguards, but it highlights the challenges that many organizations face in combating the growing scourge of “malvertising.”
Last week, I listed the various ways this blog and its author has been “honored” over the past few years by the cybercrime community, but I neglected to mention one recent incident: On May 27, 2011, several hackers who belong to a closely guarded English-language criminal forum called Darkode.com sought to fraudulently place a rogue ad on KrebsOnSecurity.com. The ad was made to appear as though it was advertising BitDefender antivirus software. Instead, it was designed to load a malicious domain: sophakevans. co. cc, a site that has been associated with pushing fake antivirus or “scareware.”
The miscreants agreed to pay at least $272 for up to 10,000 impressions of the ad to be run on my site. Fortunately, I have the opportunity to review ads that come through Federated’s system. What’s more, Federated blocked the ad before it was even tagged for approval.
I learned about this little stunt roughly at the same time it was being planned; Much to the constant annoyance of the site administrators, I secretly had gained access to Darkode and was able to take this screen shot of the discussion. The incident came just a few weeks after I Tweeted evidence of my presence on Darkode by posting screenshots of the forum. The main administrator of Darkode, a hacker who uses the nickname “Mafi,” didn’t appreciate that, and promised he and his friends had something fun planned for me. I guess this was it. Interestingly, Mafi also is admin at malwareview.com and is the developer of the Crimepack exploit kit.
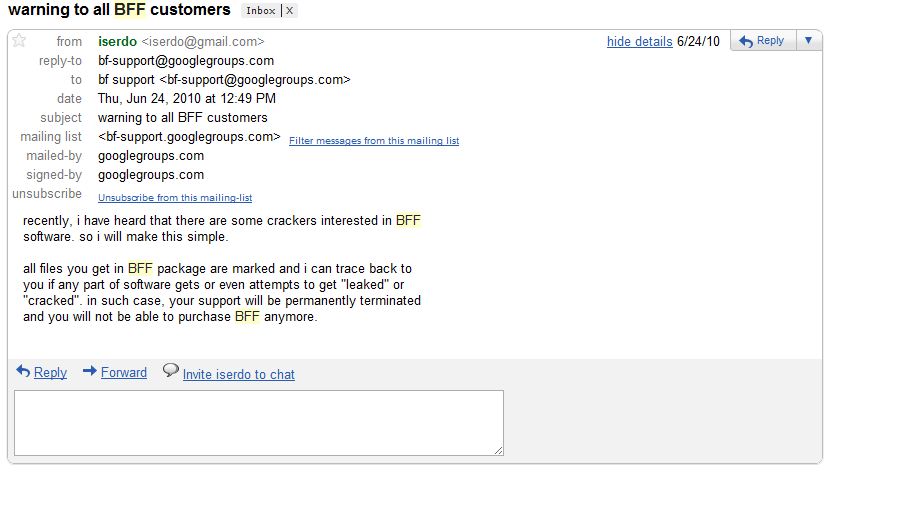
The Darkode forum launched sometime in 2008, and according to past and current members was used primarily as a support forum for the “Butterfly Bot,” a prolific bot program that was sold in the underground for several years by its creator, a hacker who used the name “Iserdo.” At some point, Iserdo sold the forum to other miscreants, and began running support for customers of his Butterfly Bot program via a Google Group called simply “Bf-Support”.
In July 2010, the 23-year-old Iserdo was arrested by authorities in Slovenia on suspicion of running the infamous “Mariposa” botnet. According to the Mariposa Working Group — a partnership between the FBI and private security firms — Iserdo sold thousands of Butterfly kits for prices ranging from $500 to $2,000. The buyers of these kits didn’t need to know much about coding or hacking; the kits allowed even unskilled hackers to create relatively sophisticated botnets.
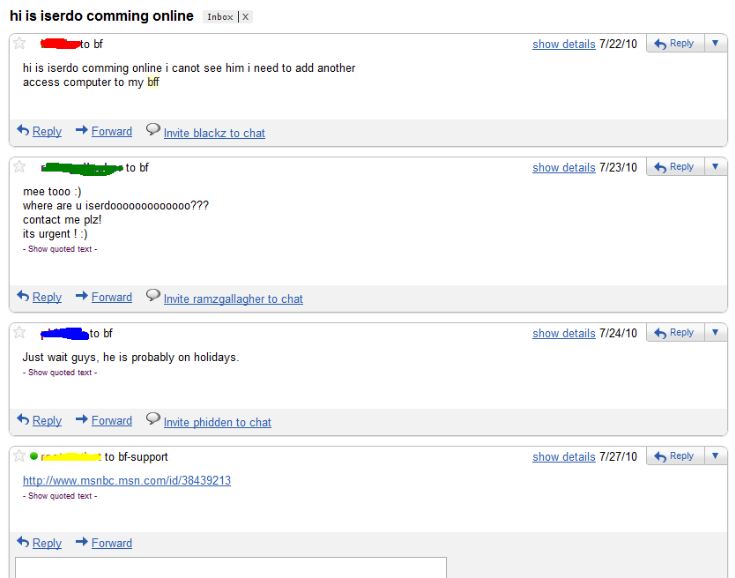
Butterfly Bot customers wonder why Iserdo isn't responding to support requests. He has just been arrested in Slovenia.
As evidenced by a recent front page story by USA Today’s Byron Acohido, malicious content embedded in online ads, or “malvertising,” is a long-standing problem that has recently taken a sharp turn for the worse: The story points to a recent analysis which documented a peak of 14,694 occurrences of malvertisements in May of this year, up from 1,533 in May 2010.
Many security-conscious readers have chosen to block ads altogether with browser add-ons like Adblock. Wholesale blocking ads can be effective in stopping malvertisements, but this approach also has the perverse effect of blocking a primary source of revenue for many sites (including this one). I have limited Federated Media to serving a very small slice of the ads on KrebsOnSecurity.com, and I am choosy about those that I let in. Add-ons like Noscript for Firefox allow users to be far more selective in which ads/scripts to allow and block.
In addition, many malvertisements rely on scripts that redirect browsers to sites that host exploit kits, software packages that probe the visitor’s browser for unpatched security flaws in popular plugins like Adobe Reader, Adobe Flash Player, Java, QuickTime and WinZip. Keeping these third-party apps up-to-date with the latest security fixes is a great way to fortify your browser against drive-bys. If you need help remembering to patch these programs, consider using a free program like Secunia’s Personal Software Inspector or FileHippo’s Update Checker.